On-Prem White Paper
Go On-Premises with DuploCloud
Introduction
DuploCloud’s platform has its roots in public cloud starting with AWS, then expanding to Azure, GCP and now on-prem. Our on-prem solution is built on top of Kubernetes and focused on containerized workloads with near term plans to integrate with on-prem compute, storage and networking vendors.
This white paper concentrates on DuploCloud’s on-prem deployment capabilities. For a more comprehensive view of our platform, refer to our DevOps Automation and Security and Compliance white papers, as well as our product documentation. DuploCloud’s on-prem capabilities enhance a vanilla Kubernetes implementation in five areas:
- Developer Self-service with No-code / Low-code Automation
- Multi-tenant Layer on Kubernetes and Multi-cluster Management
- Managed Services
- Integrated diagnostics that include Logging, Metrics and Alerts
- Built-in security controls and standards compliance
Each of these are described in detail in the subsequent sections.
Key Differentiators: Hybrid Cloud and Compliance
Many solutions provide a management layer on top of Kubernetes: Rancher, OpenShift, Rafay, etc. DuploCloud excels beyond these other solutions as follows:
Hybrid Cloud Capability
Most forward-looking organizations have a private and public cloud adoption strategy. DuploCloud has its roots as a Public Cloud automation and security solution. Organizations who adopt DuploCloud on-prem are invariably looking at a unified solution that would work for both their on-prem as well public cloud platform needs. To be clear, by hybrid cloud we do not mean deploying and managing Kubernetes clusters across a fleet of IaaS providers. DuploCloud’s public cloud offering is deeply integrated into the native PaaS (S3, MSK, SQS, etc.) and security services (AWS Guard Duty, AWS Security Hub, etc.) of the public cloud providers. DuploCloud is a complete solution for all aspects of cloud DevOps. Currently, DuploCloud integrates with 200+ cloud services and supports AWS, Azure and GCP. Core features like DevOps, Developer self-service, Low-code / No-code automation and CI/CD have been implemented in our on-prem offering and possess a level of maturity that one would expect from a company operating in the public cloud.
Security and Compliance
DuploCloud’s platform is heavily focused on security best practices and meeting compliance standards. In fact, many of our customers' initial adoption is more a function of meeting compliance standards rather than DevOps automation. DuploCloud implements out-of-box controls for several standards such as PCI, SOC 2, HIPAA, NIST, etc. The platform is integrated with a SIEM, anti-virus, host intrusion detection and dozens of other controls. These are described in detail in our DevOps Automation white paper.
Developer Self-Service with No-Code / Low-Code Automation
It’s no secret that Kubernetes is an operational beast. One needs highly-skilled and expensive DevOps engineers to build and operate a Kubernetes infrastructure. A simple deployment request from a developer might require translation into dozens of lower level complicated constructs. As an example, say we have a microservice to be set up for auto-scaling based on some simple CPU memory constraints:
- Requirement: Create a microservice with pod autoscaling with min replicas of 2 and max of 5, and CPU threshold of 80%.
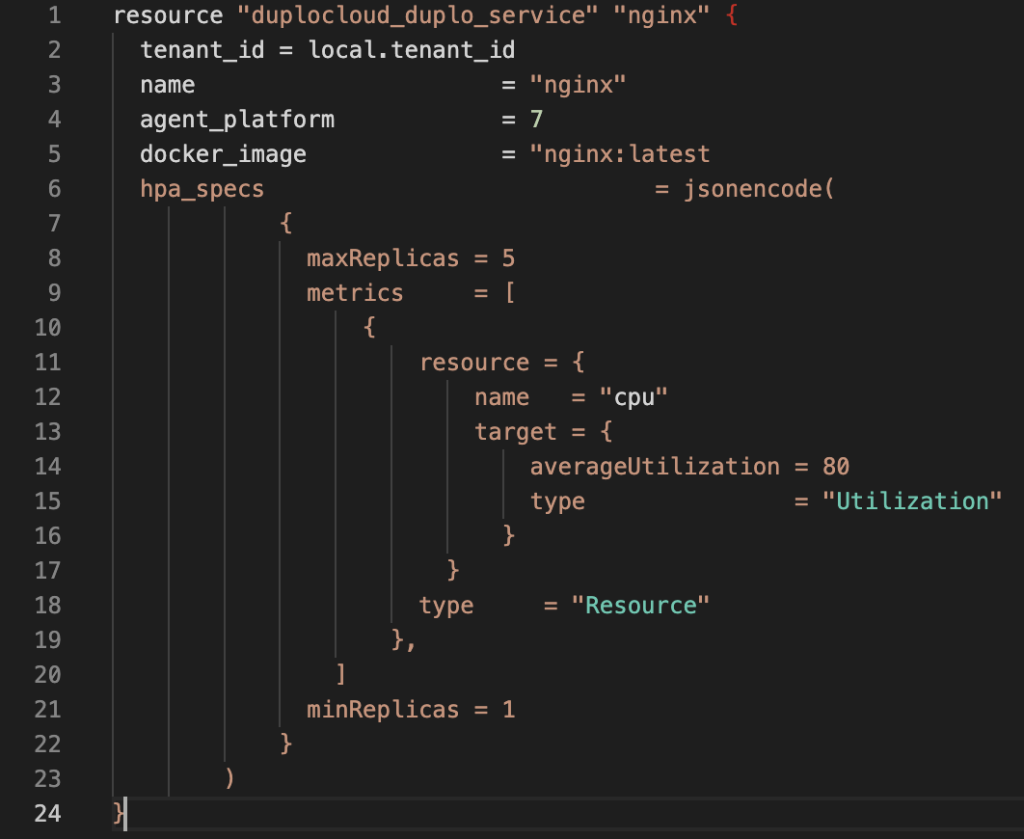
- DuploCloud Low-code Implementation: This can be achieved via DuploCloud in 20 lines of code as shown in Figure 1.
Figure 1.
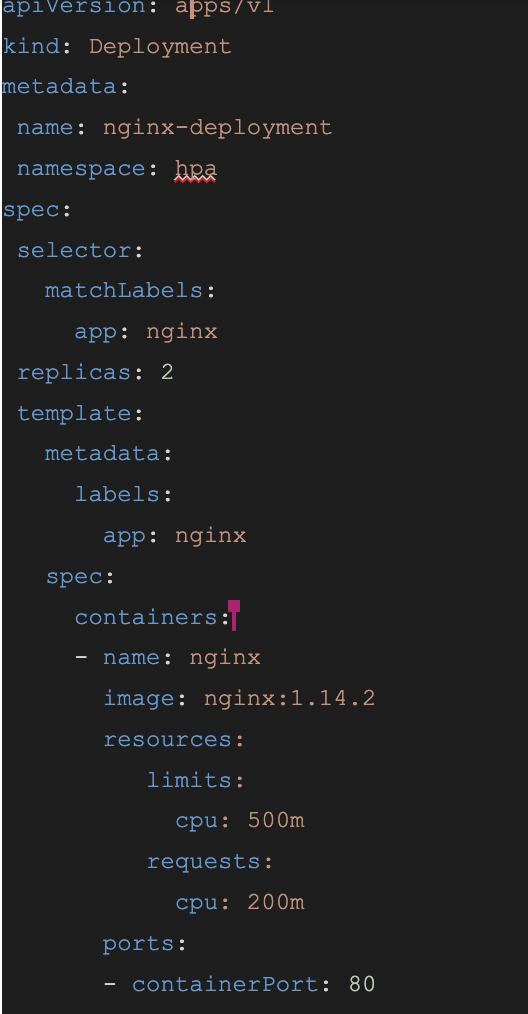
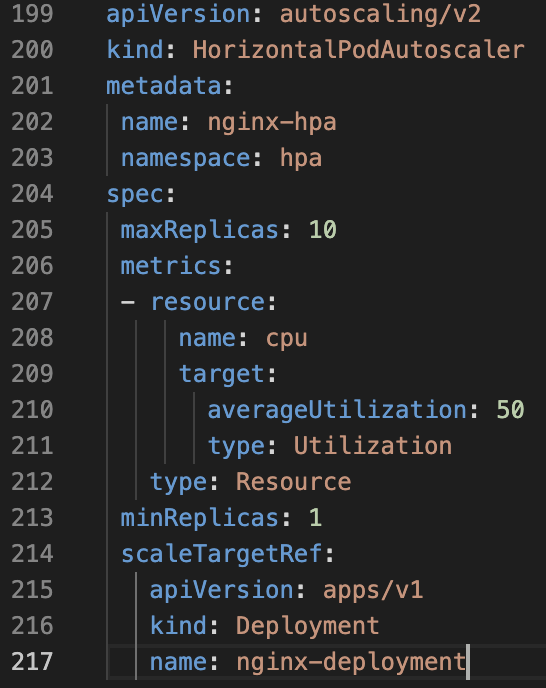
- Vanilla Kubernetes Implementation: Here it runs into hundreds of lines of code and the user has to manually clean up HPA when the service is removed. The setup for the metrics server which is done by default in DuploCloud is 200 lines per https://github.com/kubernetes-sigs/metrics-server/releases/latest/download/components.yaml and Figure 2 shows the code one has to write to enable a service with HPA:
With DuploCloud, not only has the code been reduced by an order of magnitude but the subject matter expertise required to make this setup has also been reduced substantially. There are many other such examples and concepts. DuploCloud provides an application-specific abstraction that enables a user with little to no knowledge of detailed DevOps and Kubernetes concepts to build and operate their application. DuploCloud offers both a No-code UI-based interface as well as a Low-code terraform provider.
Multi-Tenancy and Multi-Cluster Management
A Kubernetes cluster by itself is a single unit of operation. It does not come out-of-the-box with a multi-tenant concept where a cluster could be broken down into independent isolated sandboxes under different user management. It does have many lower level constructs like namespaces, service accounts, RBACs, node selectors, labels, etc. with which an operations team can try to build a layer of multi-tenancy. But it is extremely hard and requires too much effort to maintain this automation. DuploCloud provides multi-tenancy by default. There are two fundamental constructs (Infrastructure and Tenant) in our policy model as shown in Figure 3:
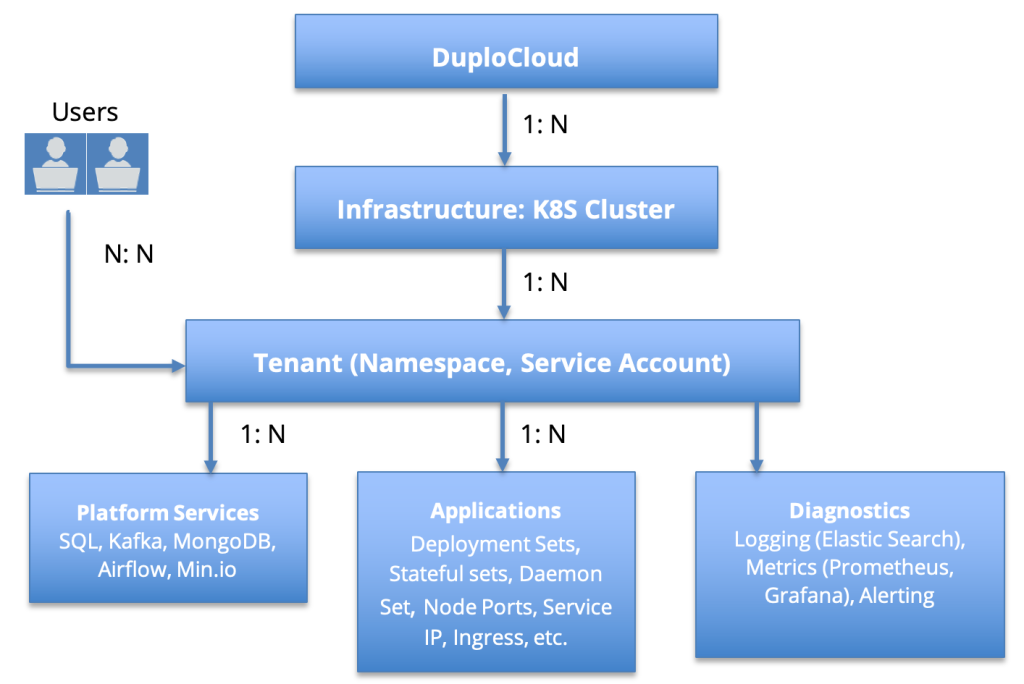
Figure 3.
Infrastructure
An infrastructure in the on-prem context is a Kubernetes cluster. The platform expects that the cluster has been set up with worker nodes added to it. Each infrastructure is a cluster name, K8S API endpoint and a token. Optionally, one can pass a data center name and other such metadata. One can add one or more infrastructures (K8S Cluster) to a single DuploCloud management portal. For a public cloud an infrastructure has more capabilities like VPC, AZs, and it can create a new cluster, etc. For details see our documentation.
Tenant
This construct is the heart-and-soul of the DuploCloud platform on any cloud provider. A tenant is a child of infrastructure and is like an isolated environment and sandbox. All resources like deployment sets, stateful sets, node ports, etc. are created within a tenant. Behind the scenes, a tenant is mapped to a namespace, service account and other isolation constructs in the parent Kubernetes cluster. A tenant is also a user access control mechanism where one user can be given access to multiple tenants and one tenant can be accessed by multiple users.
Host Segmentation
One may have a requirement where within a Kubernetes cluster we want to segment one set of hosts for some tenants and another set of hosts for other tenants. Tenants also hold hosts and such tenants have the capability to whitelist which other tenants can use their hosts. Similarly when a microservice is deployed in a certain tenant, the user can choose which other tenants’ hosts should be targeted. This is an optional feature, one can always treat the entire cluster’s hardware for all tenants.
User
A user is an end user that can be granted access to one or more tenants. An administrator will have access to all tenants.
Figure 4 shows an example multi-tenant deployment. Here the cluster has 3 nodes. We have two tenants, Tenant-X and Tenant-Y which own the nodes and there are 3 tenants (Tenant-A, Tenant-B and Tenant-C) that own the workloads. In this example, tenant-X and Y are allowed to deploy their pods in any node while Tenant-C is restricted to Node 3. Users A, B and C are scoped to Tenant A, B and C respectively. Figures 5 and 6 illustrate representative product screenshots.
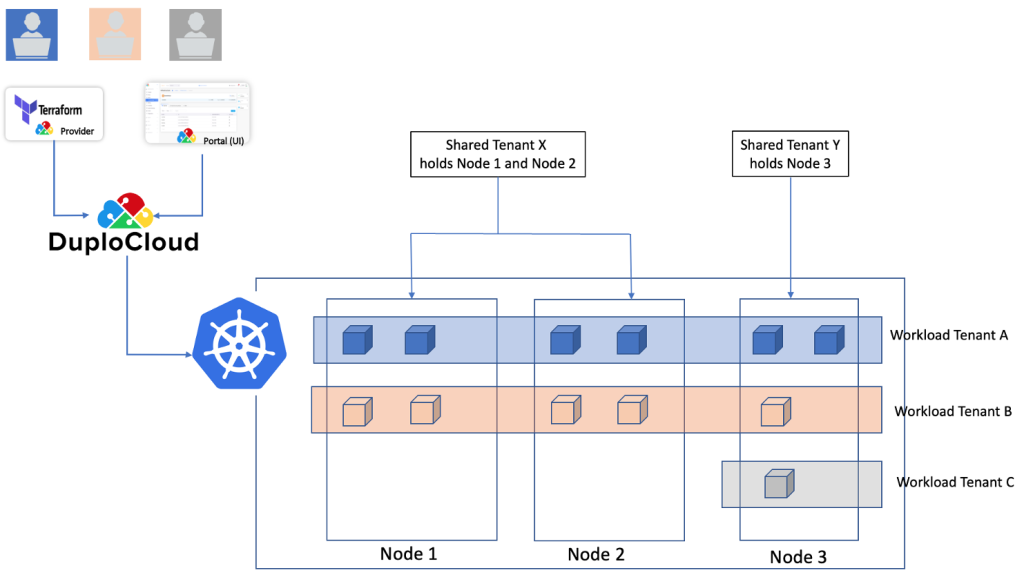
Figure 4.
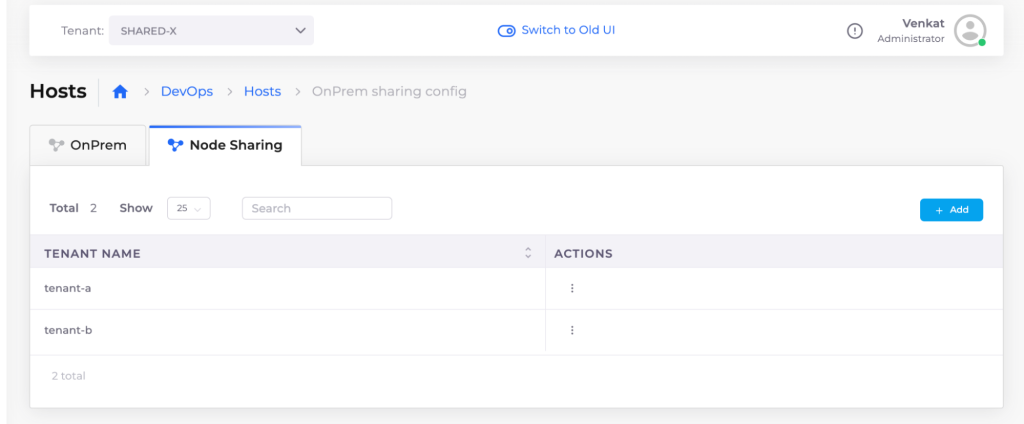
Figure 5: Node Sharing
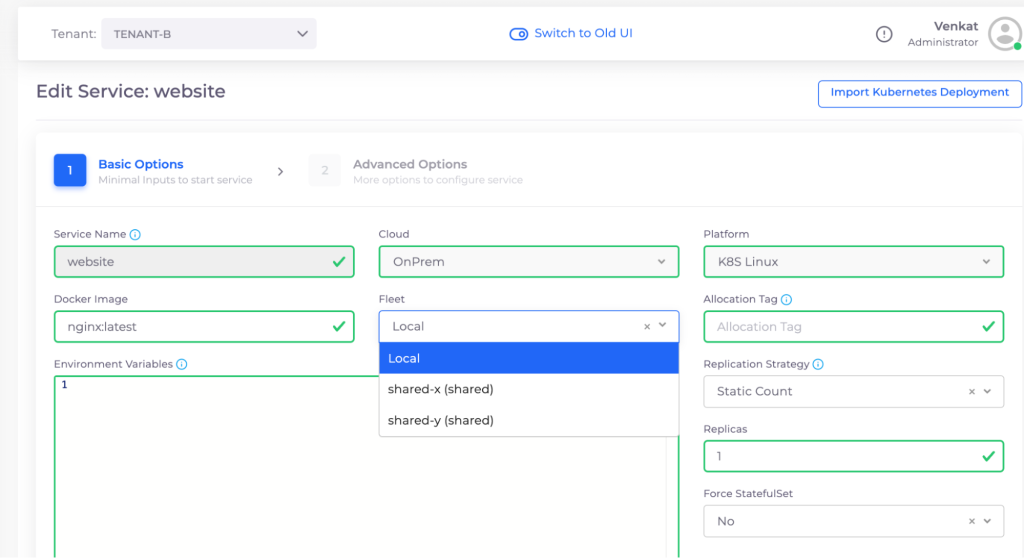
Figure 6: Choice of Worker Node Fleet during Deployment
Managed Services
Arguably the single biggest appeal of public clouds are the dozens of managed services that have been made available to users. There are two categories of services, one is open source software like MySQL, OpenSearch, Airflow, Kafka and the other are PaaS services like S3, SQS, DynamoDB, Azure Service Bus, etc. Cloud providers have optimized them for availability, performance and scale without the users having to spend cycles on them. In DuploCloud on-prem we have made several such services available and optimized out-of-the-box and ready to use. These are based on open source helm charts. Working with hundreds customers and thousands of users, DuploCloud has achieved vast experience in arriving at stable and optimized implementations. A few examples are:
- Databases: MySQL, PgSQL
- Analytics: Kafka, OpenSearch
- Storage: Min.IO
- Big Data: Spark, Airflow
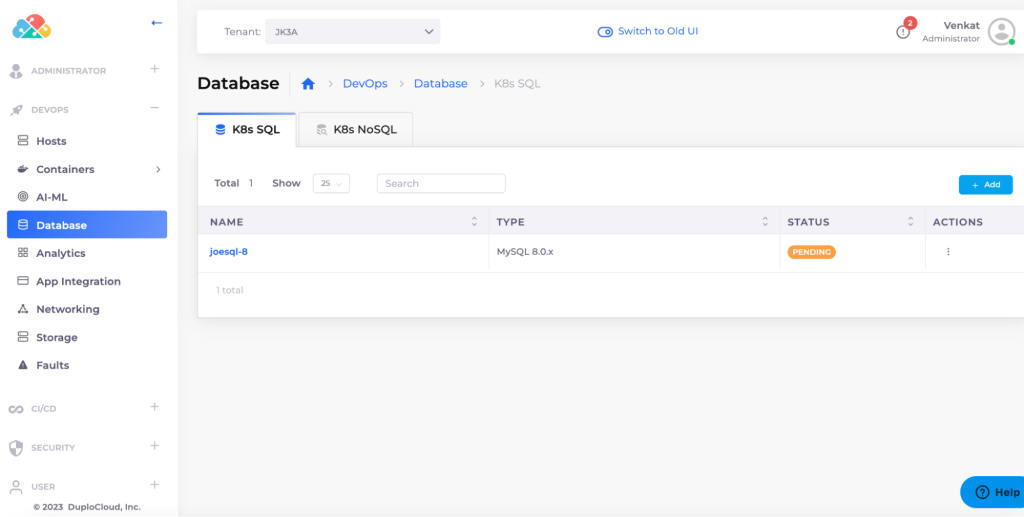
Figure 7.
We are constantly adding more services. The platform is extensible such that administrators can import their desired helm chart and any such service can be seamlessly integrated into the system.
Integrated Diagnostics: Metrics, Logging, Alerting and Audit Trail
Metrics, Logging, Alerting and Audit Trails are built-in.
Metrics
The DuploCloud platform natively provides metrics capabilities using Prometheus and Grafana. Ready-made dashboards are available per tenant for dozens of Kubernetes metrics. Behind the scenes, the platform is installing K8S metrics server, cadvisor and node exporter.
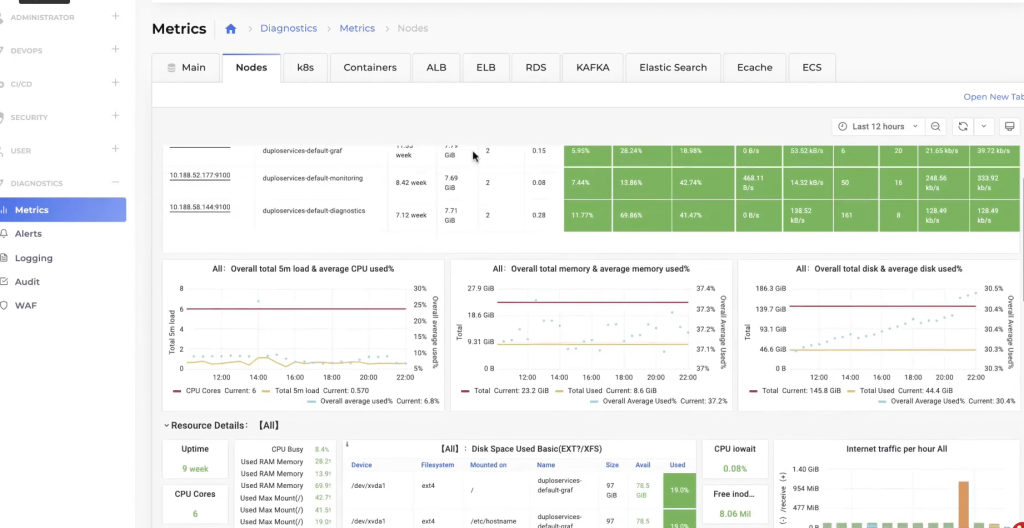
Figure 8.
Logging
Open search and file beat are used for logging capability which is also exposed per tenant in a Kibana dashboard.
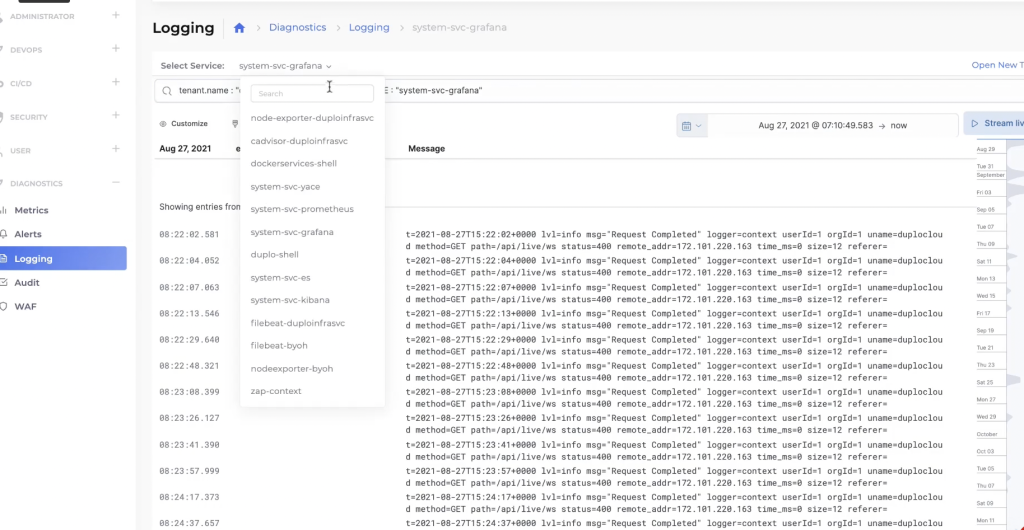
Figure 9.
Alerting
Sentry, PagerDuty and New Relic integration is available for alerting capabilities.
Audit Trails
All user actions are recorded in Open search with meta data like tenant name, user, action, service etc.
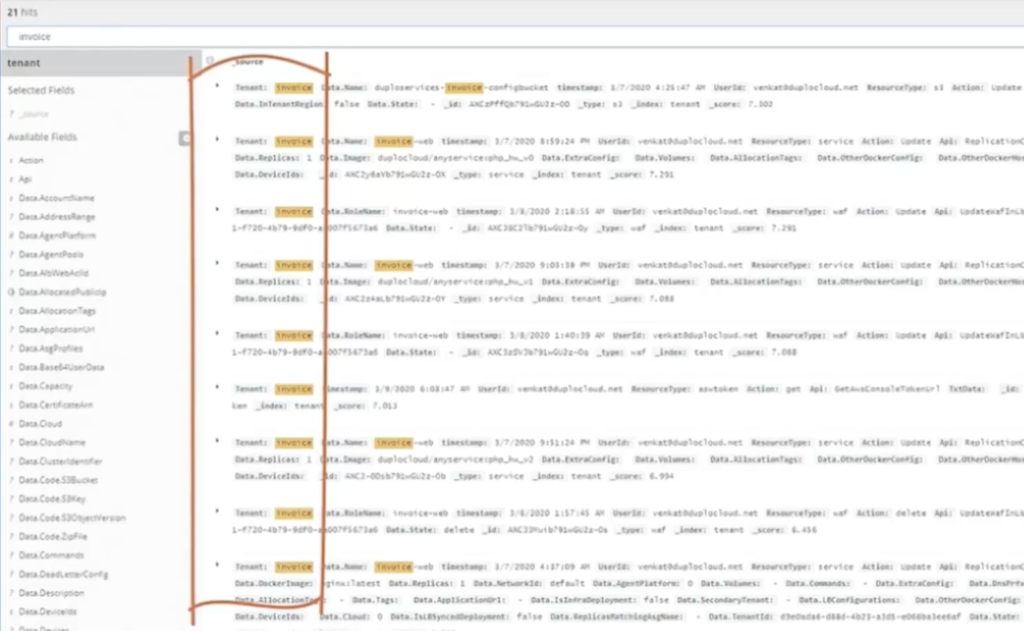
Figure 10.
Security and Compliance
DuploCloud natively implements security controls with NIST 800-53 as a reference – the operational beast. It thus subsumes PCI, HITRUST, SOC 2, HIPAA and ISO standards. The scope of these controls is the host operating system, Kubernetes and DAST. The platform facilitates SAST by offering SonarCube as a managed service. While the following is a higher level overview of the security features, a detailed whitepaper on security and compliance capabilities is @ https://duplocloud.com/white-papers/security/
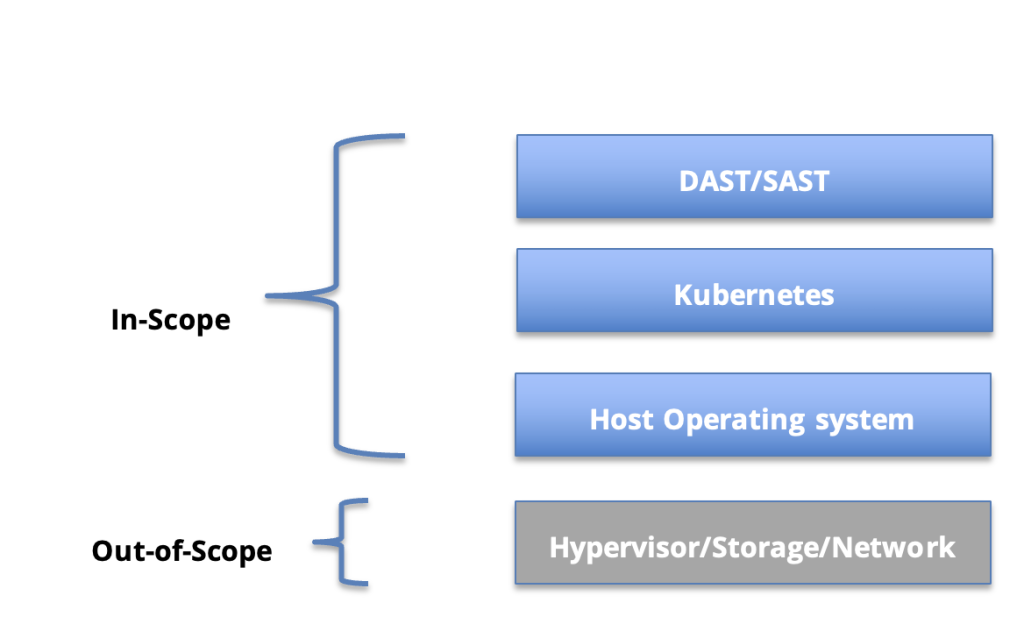
Figure 11.
Host Based Controls
The platform installs a set of agents on hosts to implement the following functionalities:
- Vulnerability Detection
- Host Intrusion Detection
- Virus scanning
- CIS Benchmarks
- File Integrity Monitoring
- Inventory Management
- Host Anomaly Detection
SIEM
DuploCloud implements a centralized system to aggregate and process all events. This is the basis of our operations and incident management. Data from the agents on hosts is centralized in the SIEM where it undergoes a set of rules to produce events and alerts displayed in an Open search dashboard. We are using Wazuh as our SIEM.
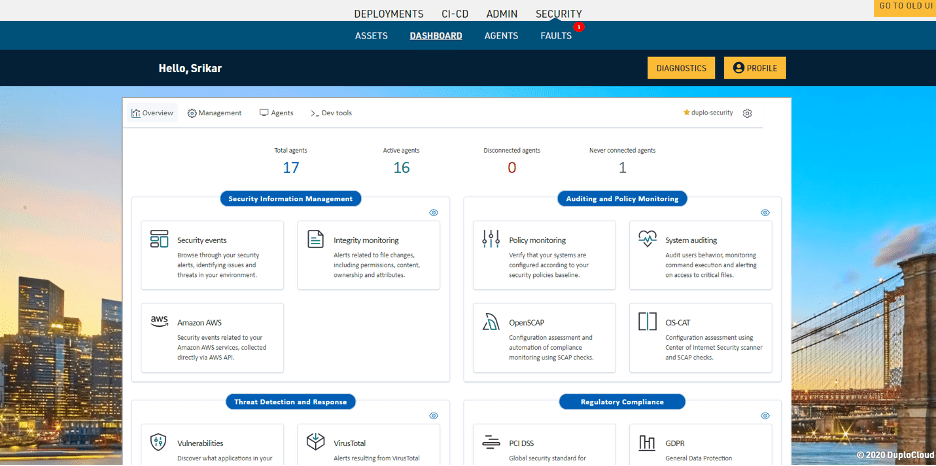
Figure 12.
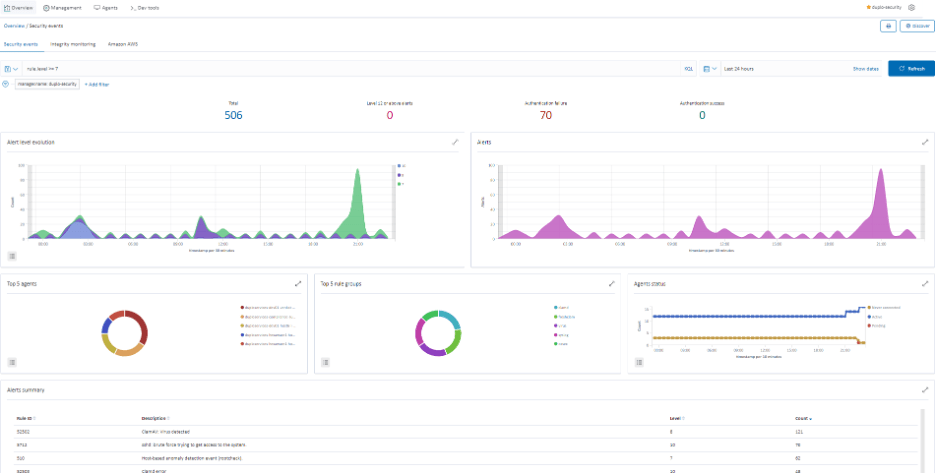
Figure 13.
Dynamic Application Security Testing
DuploCloud orchestrates ZAP for application endpoints against OWASP vulnerabilities. OWASP ZAP is an open source web application security scanner. It is intended to be used by both those new to application security as well as professional penetration testers. We configured ZAP and proxied all the URLs of the Web-Application to ZAP, which then scans and attacks the URLs and generates a report.
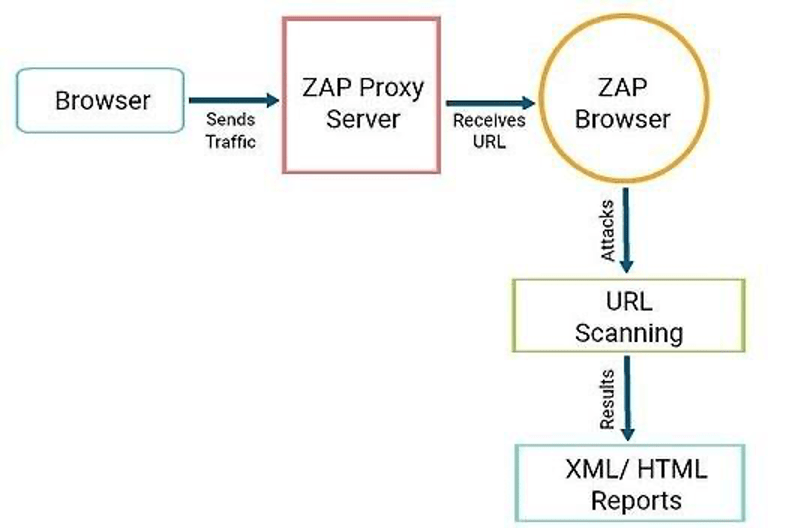
Figure 14.
Extensibility
Extensibility is an inherent goal and built into various layers of the platform.
- Any Kubernetes Provider: DuploCloud can work with any Kubernetes provider like Rancher, Anthos, Kops, etc.
- Direct deployments into K8S: Users can deploy their applications directly to the Kubernetes endpoint using Helm charts and Kubectl. As long as they are deployed in a tenant namespace, DuploCloud will import these as read-only applications and display them under the tenant. It will further provide the other capabilities like node ports, service IP, shell access, logs, metrics and alerts.
- Custom Managed Services: Administrators can import desired Helm Charts into the platform and the system will seamlessly integrate it that includes displaying it into the No-code UI.
- Custom Diagnostics Tools: The dashboards in Grafana and Kibana are available for modifications and updates. One can add new dashboards and integrate them into DuploCloud metrics dashboard as iframes. One can also use their own tools for these capabilities.
- Agent Modules: Administrators can specify a list of agents/daemons that should be run on the hosts and their uptime monitored. A typical use case for this is running security tools like Qualys, etc.
- Custom Security Tools: While DuploCloud comes with Wazuh as a SIEM, users can replace it with their desired solution.
Ability to Integrate in IaC, software and features not supported by DuploCloud: It is a common use case where users could configure some resources via DuploCloud terraform provider while for others they can go direct via their TF provider, Kubectl commands and CLI. Typical use cases include adding a custom networking policy for a namespace, configuring an on-prem router, etc. Our DevOps Automation whitepaper describes many of these example use cases in more detail.
[lwptoc]
Summary
Cloud services are convenient and powerful for end users, but their reliance on multiple services and standards means their creation mandates a much higher degree of complexity than traditional software. Extending those capabilities to on-prem with Kubernetes increases that complexity even further. At the same time, the market for cloud services has never been more competitive. Standing out with a successful product requires speedy development and deployment, and working with an effective platform such as DuploCloud can lead to up to 10 times faster infrastructure automation and compliance for cloud-native and on-prem applications.
The three key advantages of using DuploCloud are:
- 10X faster automation
- Out-of-box secure and compliant application deployment
- 70% reduction in operating costs