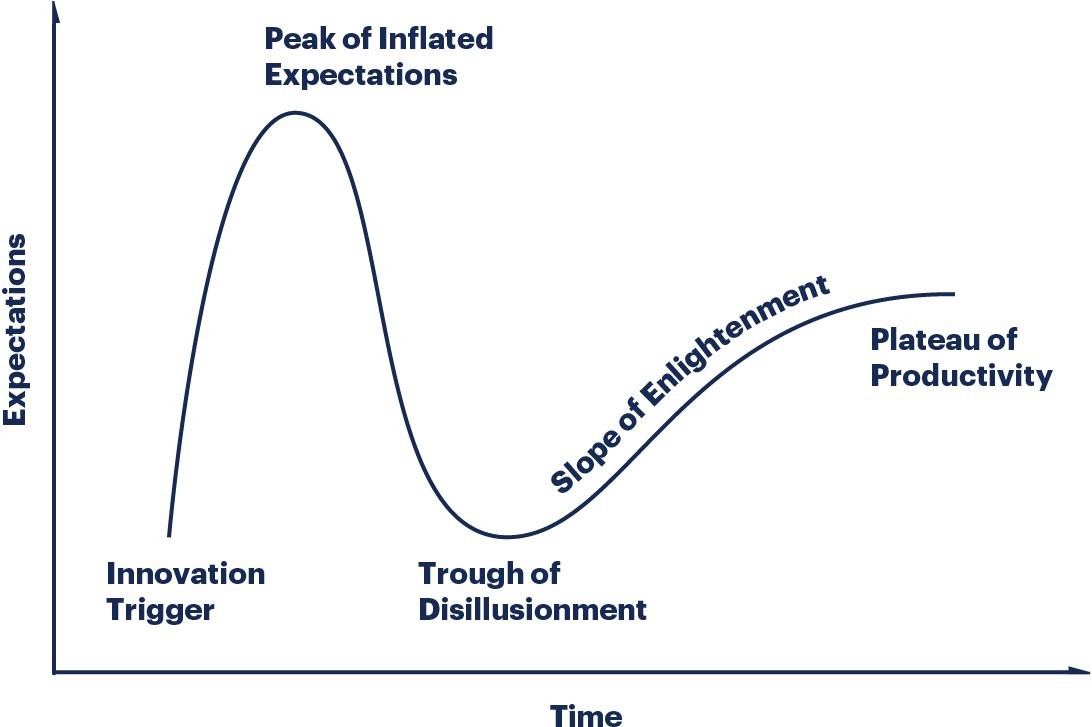
Gartner’s hype cycle for new technologies has proven accurate many times over, and cloud technologies are no different
You’ll walk that same curve when introducing cloud and DevOps into your organization. You may start with inflated expectations, but then reality hits you, and you dip into the “trough of disillusionment.
Cloud compliance is one cause of such disillusionment — when the marketing claims of push-button infrastructure give way to delays after you find out what it takes to make your cloud infrastructure compliant.
Looking up from the bottom may make the ultimate goal seem too high to reach.
But there is a way out of the “trough” without building all of your controls from scratch. Let’s take a look at the challenges cloud compliance throws at us and how automation can help you reach the productive plateau.
Why Compliance in the Cloud Is Challenging
Compliant companies have to follow a growing number of security standards. PCI, HIPAA, SOC2, GDPR, and others keep popping up. Every new standard gives rise to an exhaustive list of hard-to-implement security controls.
Cloud companies such as AWS have tried to help, but there is still a lot of effort left to companies to secure their infrastructure. Cloud providers give you the raw materials necessary to remain compliant, but you’ll have to learn how to use them.
Sharpen your architecture skills, because you’ll need them to stay compliant while taking advantage of the latest cloud enhancements.
A Cloud Compliance Case Study: PCI DSS
It may be easier to envision the scale of the compliance challenge by working through an example. PCI DSS is a typical security standard. When moving to the cloud, you’ll have to figure out how to take your compliant infrastructure and implement it using cloud technologies.
We’ll use AWS as our cloud provider in this example. Let’s walk through a few PCI requirements and how to implement each one in AWS.
Firewall Requirements
PCI has several requirements regarding network architecture and firewall barriers. For example, specification 1.1.4 calls for a “firewall at each Internet connection and between any demilitarized zone (DMZ) and the Internal network zone.”
Segmentation is the goal. Your network can’t allow traffic to move freely to wherever it wants. You need to set up rules and carefully guard sensitive areas of the system.
In AWS, we’d suggest implementing this requirement using a mixture of services. Testing, staging, and production regions of your application should each be their VPC. You’ll also need wise use of Security Groups, IAM, and Instance Profiles. Lock everything down and only open the necessary ports. WAF should protect the perimeter.
IAAS services like RDS, Elastic search should be isolated via security group. Platform services like Dynamo, S3, SQS, Secrets manager should be isolated via IAM. Lambda has one leg on Security group and another on IAM.
Identifying and Resolving Security Vulnerabilities
PCI control 6.1 states that you must have a mechanism in place to identify security vulnerabilities within your compliant systems. How can you accomplish this in AWS?
Automation is your best friend in application security. As the speed of development increases, security has to keep up. And while there will always be a place for humans to dig into applications through penetration testing to find tricky vulnerabilities, automation will help you find the “low-hanging fruit.”
AWS Inspector is an API-based service that will proactively scan and assess your application for vulnerabilities and warn you about them. It is an automatic process once set up, but it requires an administrator to choose what to test.
Other tools exist to automate application security, such as Wazuh. As with AWS Inspector, there is an effort involved in setting it up initially. But once you complete the configuration, you’ll have a constant security scan running to find vulnerabilities before they reach production. And in the event some slip in, the scans will continue to search and find vulnerabilities before attackers exploit them.
Restricting Access to Cardholder Data
PCI Requirement 7 states that you must “restrict access to cardholder data by business need to know.” You’ll need to know who has access to what within your application and when they can access it.
Restricting access in a cloud environment can be challenging because you require administrators to configure the services your application needs to work. How can you limit access while allowing the admins to do their jobs?
Orchestrating access control will require careful use of AWS Security Groups, IAM, and federated tokens. Give your admins a token for access that expires quickly. Whitelist trusted IPs for access only to the areas of your environment that are necessary for the user’s role.
The whitelist of IPs and the security groups will need to be kept up to date to make sure no holes open when personnel changes. Keep a tight grip on access control in your cloud environment.
PCI compliance can be a daunting, stressful challenge to accomplish. Download our free checklist to make sure you meet all 12 requirements:

Tracking and Monitoring
PCI Requirement 10 outlines the need to track and monitor all access to network resources and cardholder data. As your cloud environment grows, you’ll need more help to keep tabs on changes and user activity.
AWS CloudTrail can be used to track user activity and API usage. But you’ll have to make sure that CloudTrail can’t be disabled without your knowledge to hide someone’s illicit activity. AWS IAM and Config services can be used to make sure CloudTrail can’t be disabled and to alert you if it is.
CloudTrail can cover user activity, but what about infrastructure changes? You may need to bring in another tool, such as ELK, to track changes to your infrastructure. You can then marry the data from CloudTrail and ELK into a single SIEM for dashboarding, such as Wazuh.
Current State: Stitching Multiple Tools and Periodic Checks
So far, we’ve discussed how to implement PCI compliance in AWS. We’ve only scratched the surface of compliance in the cloud.
From only a few requirements, you can see that the cloud is not a “push-button” solution.
And this is only one example. Remaining compliant with HIPAA, GDPR, NIST, and the host of other standards will require the same careful planning and execution.
Currently, most organizations spend months designing and implementing their cloud architecture.
The fun cloud proof of concept you created to show off the latest amazing technology to your management stretches into months of architecture, design, and infrastructure before you get to build anything.
First, your team has to stitch together many different software tools that help with compliance. Second, you have to run periodic scans on your infrastructure and security controls after you provision your resources. They’re attempting to place band-aids on top of the holes you’ve created. Instead, applying controls during the provisioning process places a secure foundation under your developers’ code.
DevOps teams try to maintain control over infrastructure and application deployment processes to avoid any mistakes from developers. All of a sudden, developing software in the cloud begins to look the same as developing on-prem — delays, disappointment, and frustration.
Three things lead to successful cloud compliance:
- Careful planning and execution
- Automation to provision the necessary controls while you build your infrastructure
- Ongoing maintenance to adapt to changing regulations and standards
You can help developers to unlock the power and agility of cloud development while remaining compliant. But you have to enable self-service for them as much as possible while maintaining security and compliance. The only way is to give them control of doing things they want but hiding low-level details that can get them in trouble.
DuploCloud: An Intelligent Bot For Compliance Automation
Some companies may be okay spending a year (or more) coming up with the ideal cloud architecture and setting up all of the automation required to use DevOps and the cloud safely.
Here’s some of what you’ll need for AWS, for example:
- VPC/NAT Gateway configuration
- IAM and security configuration
- S3 Bucket rules
- CloudFront configuration
- Lambda functions for essential housekeeping functions
- Cloud Formation templates for every possible environment your applications require
- Datastore encryption
- Network and host intrusion detection
- Just-in-Time access
- File integrity monitoring
- Alerting
- Incident response
- Reporting
DuploCloud offers a solution for those who need compliant cloud architecture created quickly and securely. DuploCloud offers self-service to developers while automating the low-level tasks of setting up proper firewalls, security groups, access control, and installing proper tools as and when infrastructure is provisioning. Furthermore, DuploCloud’s intelligent cloud bot automatically follows all the guidelines of a well-architected design as it converts an application architect’s intent into underlying resources.
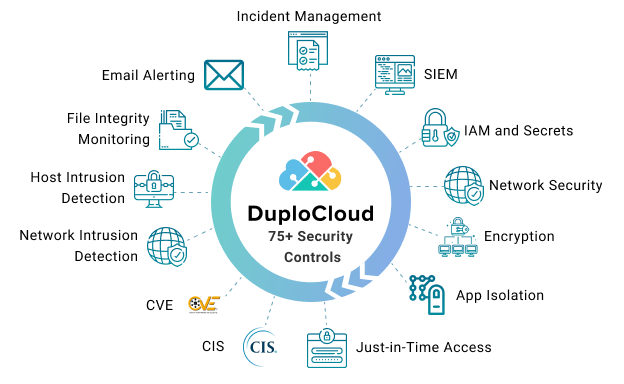
What if you could implement all of the controls necessary to remain compliant with PCI-DSS,GDPR, SOC, and HIPAA with the push of a button? That’s what DuploCloud delivers.
For example, DuploCloud maintains trails in 2 places in addition to CloudTrail. It logs all write events about infrastructure changes in an ELK cluster. A Wazuh agent tracks all activities at the host level. All 3 — CloudTrail, audit and Wazuh agent events are brought together in the Wazuh dashboard.
DuploCloud takes care of 75 out of 79 PCI Requirements for you, out-of-the-box. And that’s only one example. Similar coverage is enabled for HIPAA, SOC2, HITRUST , GDPR and many other standards. No other software we are aware of provides more than 40% out-of-coverage, leaving the rest to be done via manual automation scripts.
A core differentiation is that DuploCloud implements these during provisioning, not bolted on after the fact.
Our platform provisions compliant architecture for developers so they can develop the applications that differentiate your business.
If you’ve been frustrated by your internal “hype curve” with cloud technologies, don’t stay in the trough of disillusionment. Use DuploCloud to climb up and reach productivity with a safe, compliant architecture built for you.