SOC 2 Compliance with DuploCloud
DuploCloud is SOC 2 Compliant and our DevOps automation platform is designed to simplify, monitor, and enhance your SOC 2 compliance processes while streamlining audits.
Achieve and Maintain
SOC 2 Compliance with DuploCloud
How Can
DuploCloud Help
SOC 2 compliance is a set of internationally recognized data security, privacy, and transparency standards vital for businesses handling customer data. DuploCloud's DevOps automation platform streamlines and enhances your SOC 2 compliance processes, meeting strict security requirements while transforming compliance from a burden into a strategic advantage.
Key Features
Standards-Compliant Controls
Enhanced Security
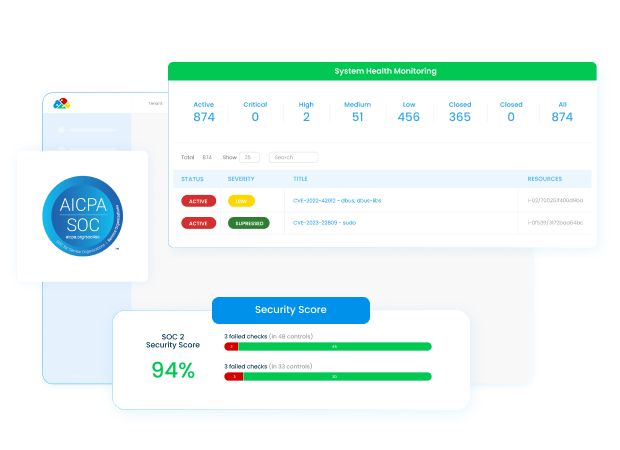
Continuous SOC2 Compliance Monitoring
Streamlined Audits
Resources
DuploCloud's resources section is packed with valuable content to help you learn more about DevOps automation and how to get the most out of our platform.
Frequently Asked Questions
DuploCloud helps simplify compliance processes, provides continual compliance monitoring, enhances security, and streamlines audits. It reduces the chance for human error and frees up resources for strategic tasks.
DuploCloud implements robust access controls in its tenant model, including identity and authentication management using IDPs like Gsuite and O365, and network segmentation. It employs instance profiles and managed identities to limit access to AWS and Azure resources, ensuring secure and compliant access.
DuploCloud orchestrates encryption for data at rest and in transit using services like AWS KMS and Azure Key Vault. It also manages encryption keys securely, aligning with SOC2 requirements for data protection.
DuploCloud integrates with Wazuh, a third-party SIEM solution, to monitor compliance and vulnerabilities. It provides infrastructure scanning, file integrity monitoring, and utilizes ClamAV for malware detection, ensuring ongoing compliance and security monitoring in line with SOC2 standards.




Ready to get started?
Boost DevOps efficiency, accelerate compliance, enhance security, and drive innovation with DuploCloud.